In the face of threats like data tampering, snooping, and identity theft, individuals and organizations require some means to ensure the safety of information that’s transmitted through private networks and over public channels. Encryption is one way of achieving this.On the surface, it sounds like a simple process: Take a message or document, scramble it, send it, and provide a method for the intended recipient (and them alone) to unscramble the information and, if necessary, communicate back.In practice for the digital age, the encryption process requires complex mathematics, secure technologies, and the use of proven techniques. Principal among these are symmetric and asymmetric encryption. Symmetric EncryptionA technique with a history that stretches back to the pre-digital era, symmetric or secret key encryption relies on the use of a secret key which is known to both the recipient and the sender of a scrambled communication. This key may be an actual word, a number, or a random sequence of characters. It’s applied consistently to the content of a message, so as to alter it in some way that makes it unreadable to casual and not so casual observers.If the secret key remains known only to the sender and receiver, they may use it to scramble and decipher any number of messages. Asymmetric EncryptionAsymmetric or public key encryption relies on a pair of connected keys.

One is private – a secret key known only to the intended recipient. Peugeot 407 remote key not working. A second, public key may be issued freely to anyone that person wishes to receive coded messages from.Documents and data encrypted with the public key may be deciphered only by using the matching private key – and applying the same encryption algorithm used by the sender.
The reverse holds in that any message encrypted with the private key requires decryption using the public key which corresponds to it. Digital CertificatesFor asymmetric encryption to work, correspondents need a secure way to find and verify the public keys they’ll use for performing cryptography on their messages.
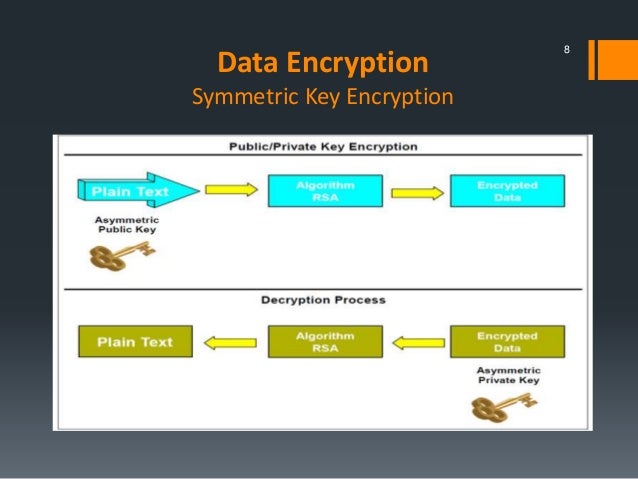
Compare Symmetric And Asymmetric Encryption
In, a hybrid cryptosystem is one which combines the convenience of a public-key cryptosystem with the efficiency of a symmetric-key cryptosystem. Are convenient in that they do not require the sender and receiver to share a common secret in order to communicate securely (among other useful properties). However, they often rely on complicated mathematical computations and are thus generally much more inefficient than comparable. In many applications, the high cost of encrypting long messages in a public-key cryptosystem can be prohibitive.